Enhancing Cybersecurity Defenses: Understanding the Red Team Assessment Process
The Red Team Assessment is designed to evaluate the effectiveness of the Customer’s information security defenses by employing real-world adversarial tactics. To achieve this, the assessment team simulates a targeted attack, attempting to gain illegal access to the external perimeter, establish a presence within the internal environment, and carry out specific objectives mutually agreed upon by the Customer and LMNTRIX. Through this process, the Customer can assess the efficacy of their prevention, detection, and response capabilities. Possible objectives might involve accessing customer data, compromising internal domain administrator credentials, or showcasing access to email or critical business systems. To ensure a realistic assessment, the test will be executed without any prior information or access to the Customer’s IT environment. LMNTRIX will employ tactics crafted to bypass detection by IT security teams and controls, providing a comprehensive evaluation of the organization’s security posture.
The specific methodology used during this testing may be customized during the engagement based on results and findings but will generally follow the steps below:
Step 1 – Identification
The goal of this step is to identify, assess, and catalog both human and technical targets that would be most susceptible to compromise by an external adversary.
- LMNTRIX may leverage both open-source intelligence collection techniques (OSINT) and active scanning tools to locate Internet-accessible systems and applications. Each potential target may be evaluated for further testing based on multiple factors, including exposed ports and services, technical architecture, functionality, potential vulnerabilities, ease of compromise, and value to an attacker.
- LMNTRIX may also leverage OSINT to identify potential Customer employees for targeting using social engineering techniques. This process entails the collection and analysis of data derived from publicly accessible sources such as search engines, social media, Customer websites, and other online resources that provide the information necessary to create and execute targeted social engineering attacks against specific individuals.A master list of the potential targets will be the outcome of the Identification phase. These are the targets that will be evaluated and prioritized for exploitation.
Step 2 – Exploitation
During the Exploitation phase, LMNTRIX will leverage the analysis conducted during the Identification phase to select high-potential targets, customize technical and social engineering attacks designed specifically for those targets, and execute the attacks in order to gain access to internal Customer networks. The Exploitation phase may include any of the following:
- Technical Exploitation – Once LMNTRIX identifies vulnerabilities in Internet-facing systems and applications, they may try to exploit these weaknesses to compromise sensitive data or to gain unauthorized access within a network perimeter. Furthermore, they may execute attacks to gather more information about the environment, including discovering additional targets or gathering more information about existing targets. Types of attacks typically used during this activity include SQL Injection, upload and execution of web shells, and brute force attacks against login interfaces.
- Social Engineering – LMNTRIX may use phone and email-based techniques to target Customer employees. Individuals may be selected from the target list based on job function, presumed access to important internal systems, and perceived susceptibility. LMNTRIX will tailor the phone and email-based attacks to each user in an attempt to perform various potentially harmful actions, including revealing login credentials, visiting unknown websites, or executing malware on the target’s corporate IT asset.
The Exploitation phase aims at breaching the perimeter and accessing the internal system. Technical exploitation involves compromising Internet-facing systems and then using that access to target neighboring systems within the environment. On the other hand, social engineering exploitation involves acquiring valid credentials to access the environment remotely, such as through VPNs or executing malware on the user’s device, allowing LMNTRIX to operate within the internal environment with the user’s permissions.
Step 3 – Post-Exploitation
After successfully infiltrating the internal environment, LMNTRIX will try to move laterally across the intranet to achieve the predetermined objectives. In the Post-Exploitation phase, they may engage in the following activities:
- Privileged Escalation – Immediately after LMNTRIX gains access to a system, they may use different methods to increase the privileges of the current user to the highest levels. These privileges will enable LMNTRIX to carry out various harmful activities. This includes establishing persistence, adding more malware like key loggers, and capturing credentials.
- Internal Exploitation – By leveraging the same techniques used during the Identification phase, LMNTRIX may search for internal data repositories, portals, collaboration forums, and other internal sources that provide access to sensitive data and assist in locating high-value targets within the intranet. Furthermore, LMNTRIX may pinpoint internal systems vulnerable to technical exploits, which can gain deeper access to the environment or acquire additional credentials.
- Credential Harvesting – Once access to internal systems has been obtained, LMNTRIX may begin collecting account credentials for valid internal users. Specific focus will be given to identifying and extracting privileged domain credentials, as these provide extensive access to the environment. Common credential harvesting attacks involve extracting information such as hashes, Kerberos tickets, and clear text credentials from local system memory or accessible virtual machine files. Additionally, attackers may identify scripts and configuration files containing hard-coded credentials for unauthorized access.
In many cyber attacks, the post-exploitation phase is a repetitive process. It includes identifying internal targets, compromising them, and extracting more information and credentials to move laterally within the intranet. As mentioned earlier, the main aim of this phase is to achieve the predetermined attack goals. In order to achieve the objectives, LMNTRIX often obtains full administrative access to critical systems (e.g., financial application servers, key databases, executive email, and file shares), the internal authentication and authorization systems (e.g., Active Directory, LDAP, two-factor authentication), or the core network infrastructure (e.g., RADIUS, TACACS).
Another goal of this evaluation is to assess the ability of the information security team to discover and respond to threats. To achieve this, LMNTRIX will employ testing methodologies and attack strategies specifically designed to bypass or evade existing security measures. LMNTRIX will leverage custom malware that may not be detected by commercial anti-virus products and avoid using any scanning or exploitation techniques that are likely to be observed by system users or detected by network sensors and endpoint controls. If the Customer information security team discovers the ongoing test, LMNTRIX and Customer project managers will collaborate to determine the most suitable approach for continuing the testing process.
At the project kickoff meeting, Red Team activities will be thoroughly discussed and mutually agreed upon by both LMNTRIX and the Customer. This may include the scope of the engagement, such as whitelisted and blacklisted targets. Moreover, the approval and coordination procedures required prior to exploiting targets, schedules and timeframes, data handling and communications, and the escalation policy will also be established.
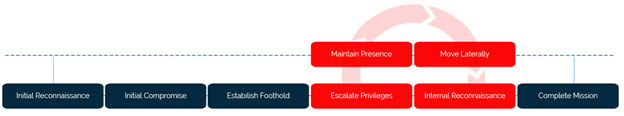
In each engagement, your organization’s readiness and responsiveness to cyber attacks are tested by using real-world attacker tactics, techniques, and procedures (TTPs). These engagements follow the phases of the attack lifecycle.
Red Team Cyber Security Assessments at a Glance
WE HELP YOU:
- Assess the effectiveness of your security team in dealing with a cyber attack
- Train your team to strengthen their response to future cyber attacks
- Measure the effort needed to breach your sensitive data or IT infrastructure
- Spot and resolve complex security gaps before an attacker exploits them
- Obtain data-driven risk analysis and improvement guidance
WHAT YOU GET:
- A concise executive summary of the assessment carried out by the Red Team tailored for executives and senior management.
- A comprehensive report outlining all assessment actions and discovered vulnerabilities.
- Fact-based risk analysis explaining the significance of each vulnerability in your environment, along with methods to confirm them.
- Strategic recommendations aimed at long-term improvement.

